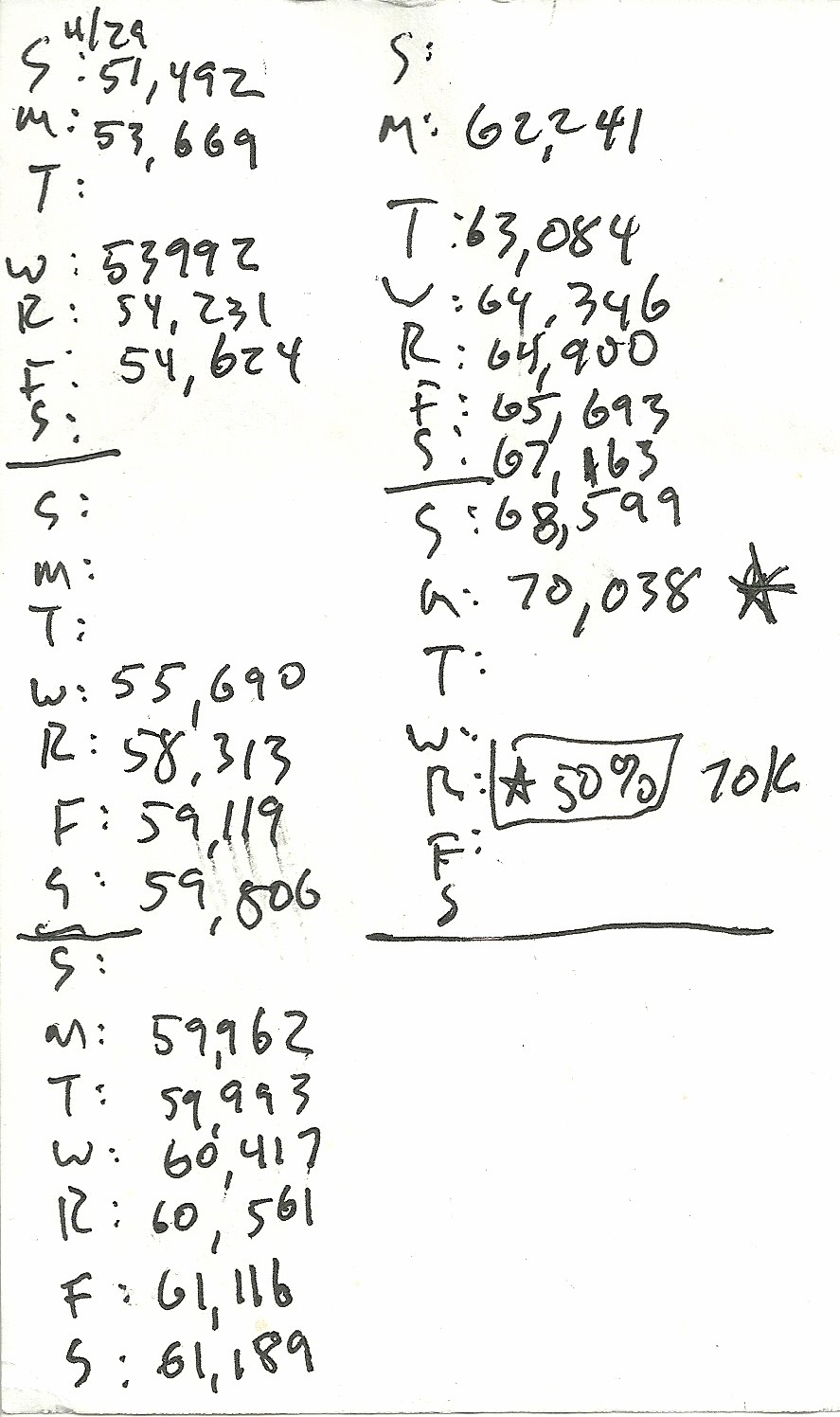
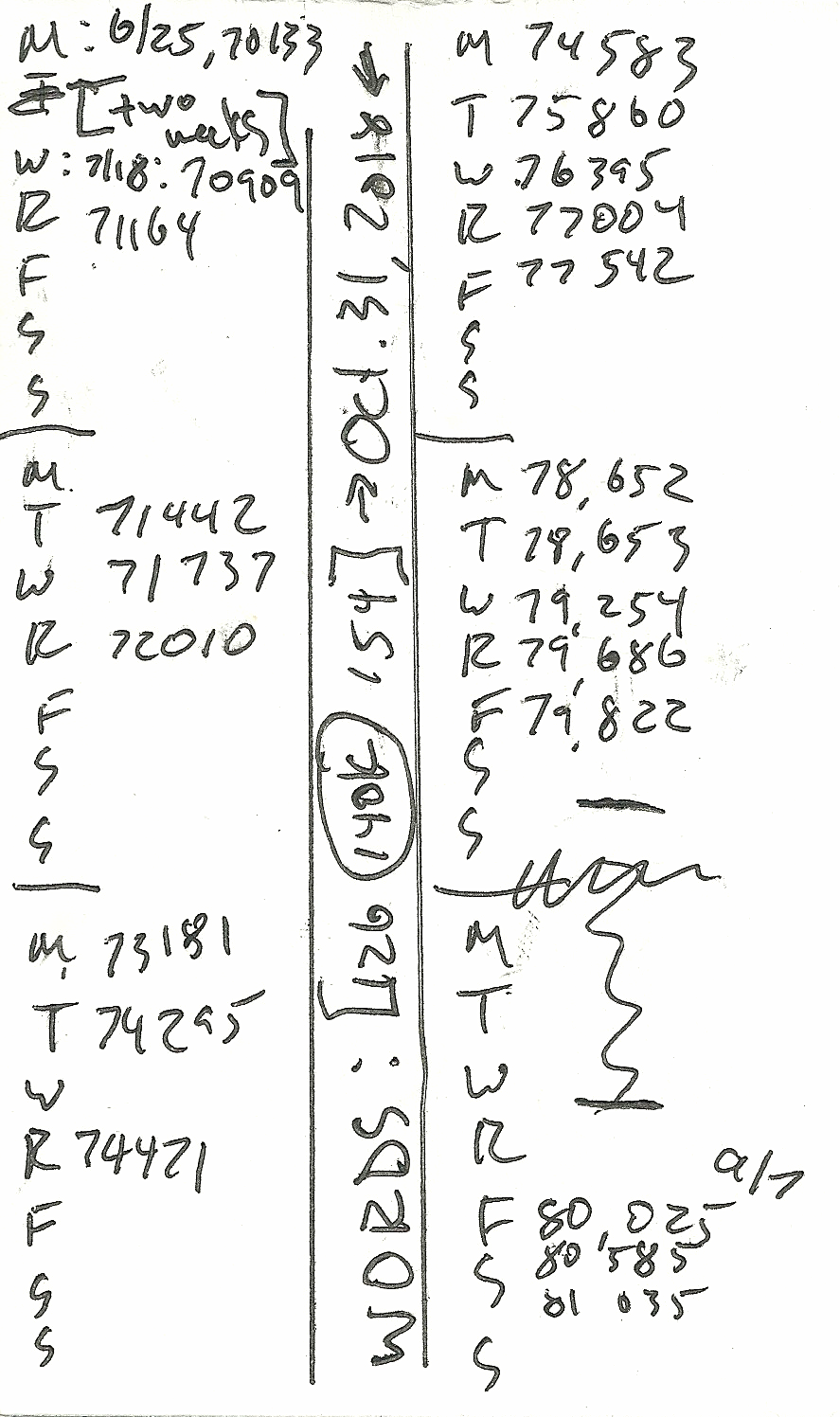
Here’s the data I collected about myself over the last year: daily word count on my book manuscript, written on index cards, starting March 25 and stopping today.
.

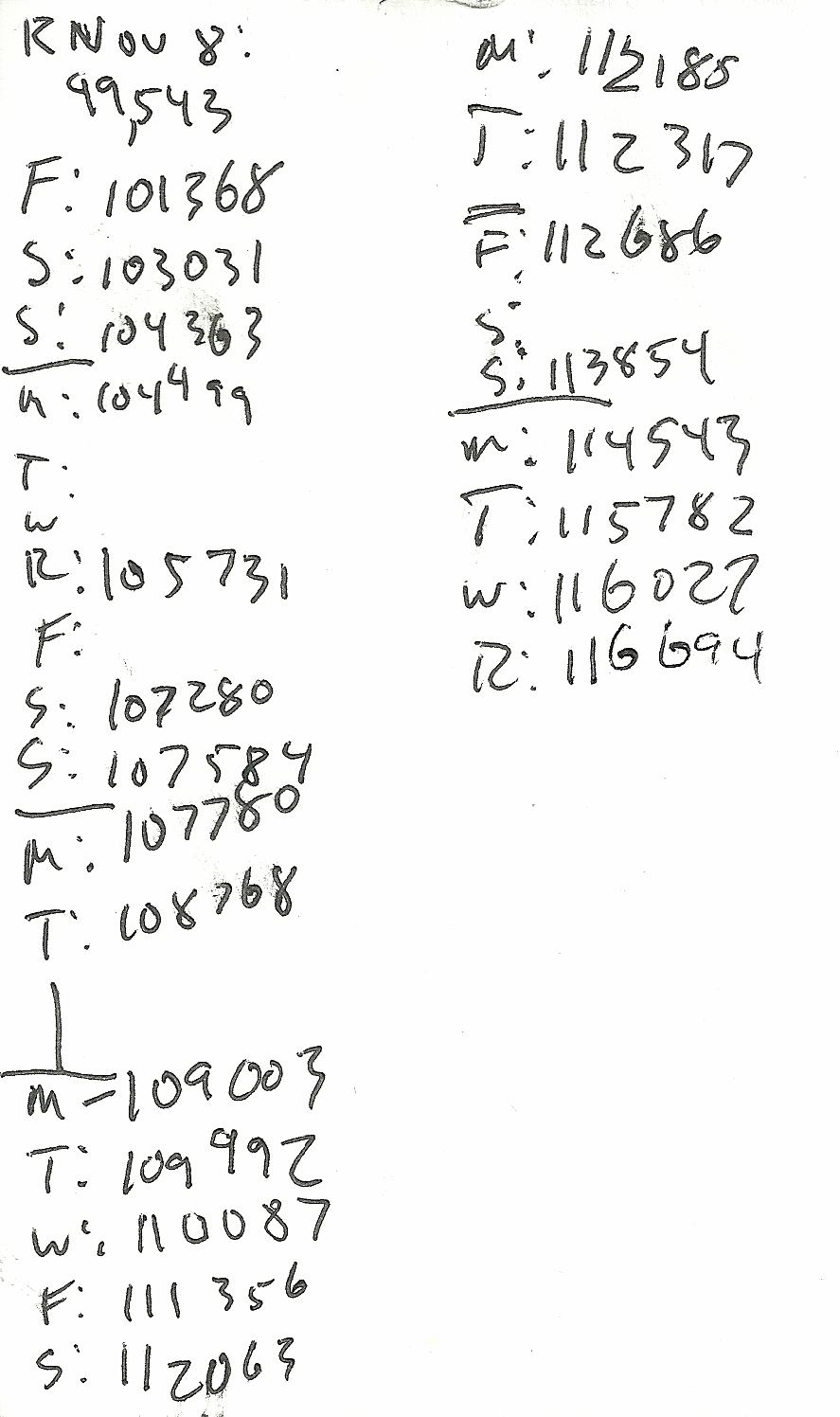
Author Archives: Kevin L. Ferguson
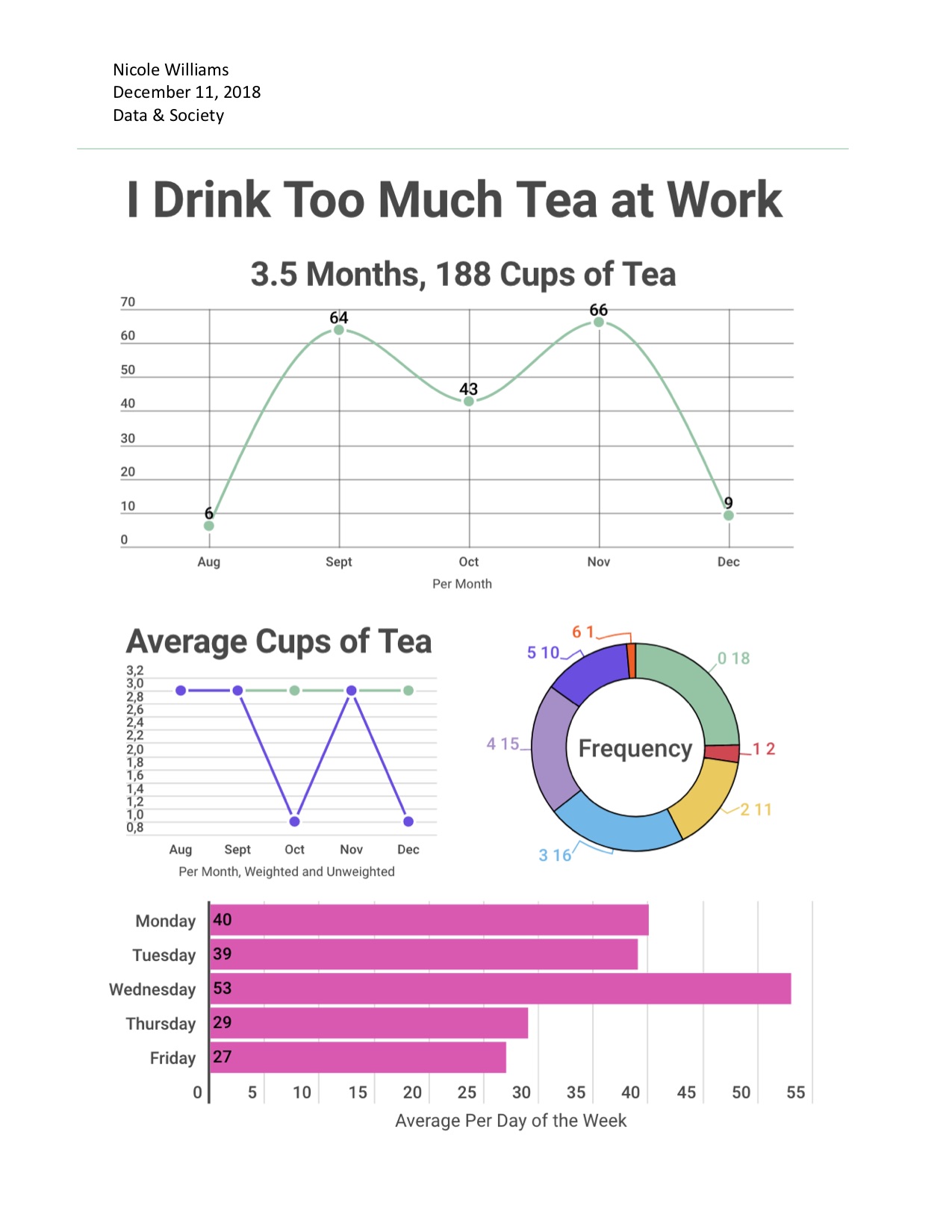
Nicole Drinks Too Much Tea
Algorithms of Oppression
Introduction
• technological redlining and algorithmic oppression
• big data and algorithms are anything but benign, neutral, or objective
• “glitches” don’t suggest that the “organizing logics of the web” are broken, but instead something just going wrong with a “near-perfect system.”
• “Google’s position is that it is not responsible for its algorithm.”
Searching for Black Girls
• lack of diversity framed as “pipeline” issues in hiring, instead of racism and sexism
• “search engine results perpetuated particular narratives that reflect historically uneven distributions of power in society.” (71)
• theories of racial formation vs. theories of structural white supremacy (79)
• “white supremacy as the dominant lens and structure through which sense-making of race online can occur” (84). “just google it.”
• “Google/Alphabet is a broker of cultural imperialism that is arguably the most powerful expression of media dominance on the web we have yet to see.” (86)
• “contextualize information as a form of representation, or cultural production, rather than as seemingly neutral and benign data that is thought of as a ‘website’ or ‘URL’ that surfaces to the top in a search.” (106)
Searching for People and Communities
• “cloaked websites”
• “search results belie any ability to intercede in the framing of a question itself” (116)
• “search engine results also function as a type of personal record and as records of communities” (116)
Automating Inequality
3. Homelessness on Skid Row
• coordinated entry system: prioritization and “housing first” (vs. “housing readiness” 92–93)
• VI-SPDAT: Vulnerability Index—Service Prioritization Decision Assistance Tool
• data used for what? (114)
• community policing (118–119)
• coordinated entry is both a system for managing housing and a system for surveillance. (121)
4. Allegheny Algorithm
• “predictive risk models”
• AFST “training” the intake workers (142)
• proxies for child abuse: community re-referral and child placement
• outcome variables, predictive variables, and validation data (143–145) How do these design flaws lead to limited accuracy?
• referral bias (153, 154)
• AFST best-case scenario (171)
habeas data
Introduction
• d-order: warrantless search of provider for who, when, and where information, meta-data.
• third-party doctrine: individuals “relinquish reasonable expectation of privacy when they transact via a third party”
• license plate readers (LPRs)
• world’s first data protection law, 1970, Germany. requires “consent” to collect/use personal data.
• habeas corpus –> habeas data (xvi)
Ch. 6: email
• Warshak v. US: must have warrant before ISPs turn over email content
• 1986 Electronic Privacy Communications Act (EPCA). two outdated aspects: distinguished between “remote” and “electronic” computing services.
• pen/trap: used to get electronic content
• what was Levison’s primary concern, leading him to refuse to comply with order giving TLS keys?
• what are some reasons tech companies like Google and Facebook decided together to demand ECPA warrants from the government?
• how has “the plummeting costs of storage . . . flipped the default understanding of how surveillance threatens privacy?” (143)
Ch. 9: phone searches
• “search incident to arrest” is exception to warrant rule.
• Smallwood v. Florida: cannot search cell phone without warrant
• Riley / Wurie vs. US: argument was that “digital was different” (206)
• fingerprints vs. PIN codes: Fourth and Fifth amendments
• foregone conclusion exception to Fifth amendment
• lawful hacking and NITs (216)
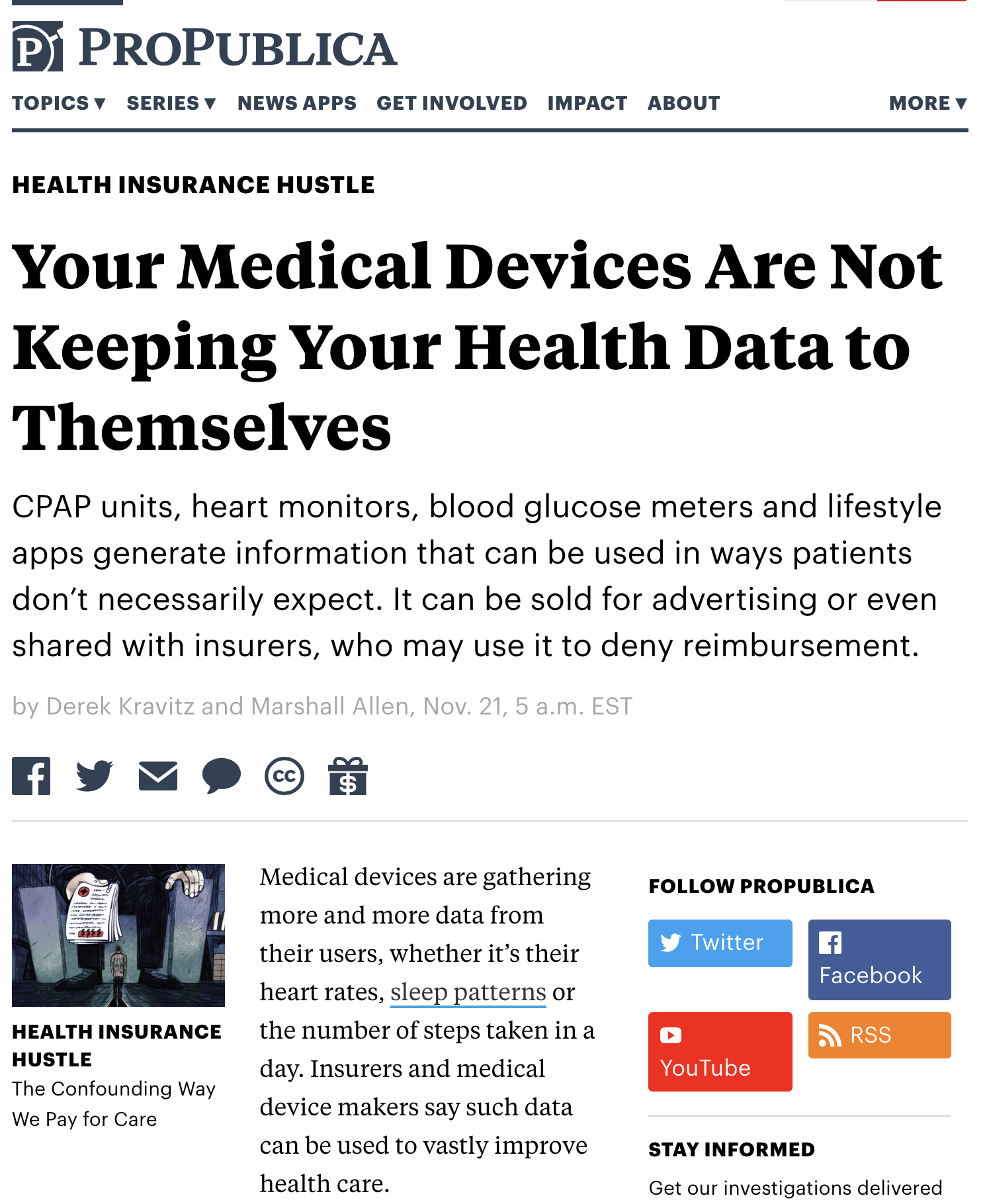
Medical Data (relevant to Nicole?)
Final Projects!!!
 Some choices for your final projects:
Some choices for your final projects:
• A final paper
• A data project
• Something experimental
By next week, send me a proposal:
Typed, about a page, with a tentative title.
Your proposal should include (1) a clearly articulated research question or problem, (2) a purpose or justification for your project, (3) what methodology or discipline you will use, and (4) 3–5 sources.
Some examples:
• Expand on your in-class presentation
• Build a data-interfacing wearable using Arduino Lilypad and write a description of its purpose
• Write a data manifesto for a company like Google and Amazon, based on a recent problem
• Create an analysis of the media infrastructure of our classroom, with recommendations for improvement
• Analyze the media infrastructure of your home.
• Use the data you’ve been collecting this semester to tell a story about datafying yourself.
• Tell a story with data by doing a data analytics project including an editorial with visualizations.
Please leave questions/clarifications as a comment
Not Really Sure Where to Start with This . . .
Signal Traffic
Introduction
• signal traffic
• “the content and form of contemporary media . . . are shaped in relation to the properties and locations of these distribution systems” (1).
• how content moves and how movement affects content’s form.
• layering, path dependencies of “media infrastructures”
• “infrastructural disposition”:
(1) processes of distribution (not production emphasis)
(2) materialities of distribution
(3) tech literacies and public involvement
• Scale, Relationality, Difference and Unevenness, Labor/Repair/Maintenance, Natural Resources/Environment, Affect, Innovative Methodologies
Data Centers and the Cloud
• the cloud’s transparency as political metaphor? (75)
• media no longer a public good? (79)
• not just what is deliberately hidden, also what is made hypervisible (80)
Fixed Flow
• “Analyzing cables as media infrastructures involves articulating how they invisibly contort the conditions of possibility, geographic dispersion, and cultural perception of media signals” (55).
• (1) Cables “function as a resource for mediation” (loop)
• (2) Cables alter “the temporality of information exchange”
• (3) Cables “implicate users within new and unseen structures of power” (disruption)
• (4) Cables “can perpetuate imbalances in media production and consumption” (inequality)
• “The user is not a rational agent who can locate herself in relation to such infrastructure; rather, she is a posthuman subject that extends across the network in multiple, unpredictable ways, intertwined with developments that are beyond any individual’s knowledge or control” (67).
Platform Capitalism and Bitcoin
Platform Capitalism
• digital economy: (1) most dynamic sector, (2) systematically important, (3) presented as an ideal
• what does it mean to live in a knowledge economy? (22)
• how does data [“datafication”] come to serve key capitalist functions? (24)
• Characteristics of platforms:
– (1) “the basic infrastructure to mediate between different groups.” (25)
– (2) reliant on “network effects”
– (3) use “cross-subsidisation”
– (4) appear an empty space, actually embody a politics
• Platforms are “a new type of firm,” an “extractive apparatus for data” (27)
– (1) Advertising platforms (Google, facebook)
– (2) Cloud platforms (AWS, Salesforce)
– (3) Industrial platforms (GE, Siemens)
– (4) Product platforms (Rolls Royce, Spotify)
– (5) Lean platforms (Uber, Airbnb)
• So, what are the specific factors leading to the rise of platform capitalism? Which platforms will be successful in the future and which less so?
Politics of Bitcoin
• five right-wing talking points about central banking (2)
• blockchain as a platform?
• cyberlibertarianism: “governments should not regulate the internet,” “freedom will emerge inherently from the increasing development of digital technology.”
• however, cyberlibertarianism incorporates right-wing worldview even when seeminghly manifesting liberal commitments
• “freedom” and “government” redefined (4)
• Big tech’s similarity to old extraction industries •••